The threat:
The recent pro-Palestinian protests and activities across Europe and the US are part of a wider tactic of activist campaigns.
Many of those involved in these activities can be considered professional activists and agitators. This can be evidenced by the many banners and paraphernalia visible during the protests.
As part of this latest campaign, several companies were named as legitimate targets by Palestinian Action during a recent Zoom workshop attended by supporters.
The purpose of its workshop was “to inform people of British complicity with apartheid Israel” and alert them to its different “campaigning methods”. Some of the companies referred to have already been targeted and direct action taken.
Palestine Action was founded in 2020 by Huda Ammori, an ex-campaign officer for the Palestine Solidarity Campaign, and Richard Barnard, a former Extinction Rebellion activist. It is because of this that the tactics used can be expected to mirror those practices by other activist groups.
In one example, the Animal Liberation Front claimed responsibility for a powerful fire bomb that was mistakenly placed on the doorstep of a neighbour.
The targeting of executives’ homes and private lives was a tactic practised by animal rights extremist groups as far back as the 1980’s.
More recently AQ encouraged this tactic via their banned publications Inspire.
Inspire 15 focuses on home assassinations, rather than encouraging workplace attacks as it has done previously, specifically calling on jihadists to damage the American economy by killing business leaders and entrepreneurs in their homes, which are perceived to have less security than places of business. The magazine also urges followers to emulate the Palestinian street-killing of Jews.
AQ Inspire 2016 stated “taking a quick comparison between assassinating the target at home and at a workplace. At home, there is less security than at the workplace”.
It is accepted that the information of any targeting may not also be a physical threat. Reputational harm together with intimidation are often the objective.
In August 2023 the UK Prime Minister’s home was targeted by Greenpeace.
It is known that such activists and other fixated individuals when targeting specific individuals will conduct extensive OSINT to identify any vulnerabilities their target/s may have and can be quite patient when planning their intentions.
Attack Planning
Those individuals who targeted organisations and prominent people don’t just snap and decide to conduct their attack in one day. They are fuelled by a grievance that for them, cannot be resolved peacefully. In their minds the only way to resolve their grievances is through direct action, be that violence, disruption, reputational harm etc depending on the grievance, the person and the cause.
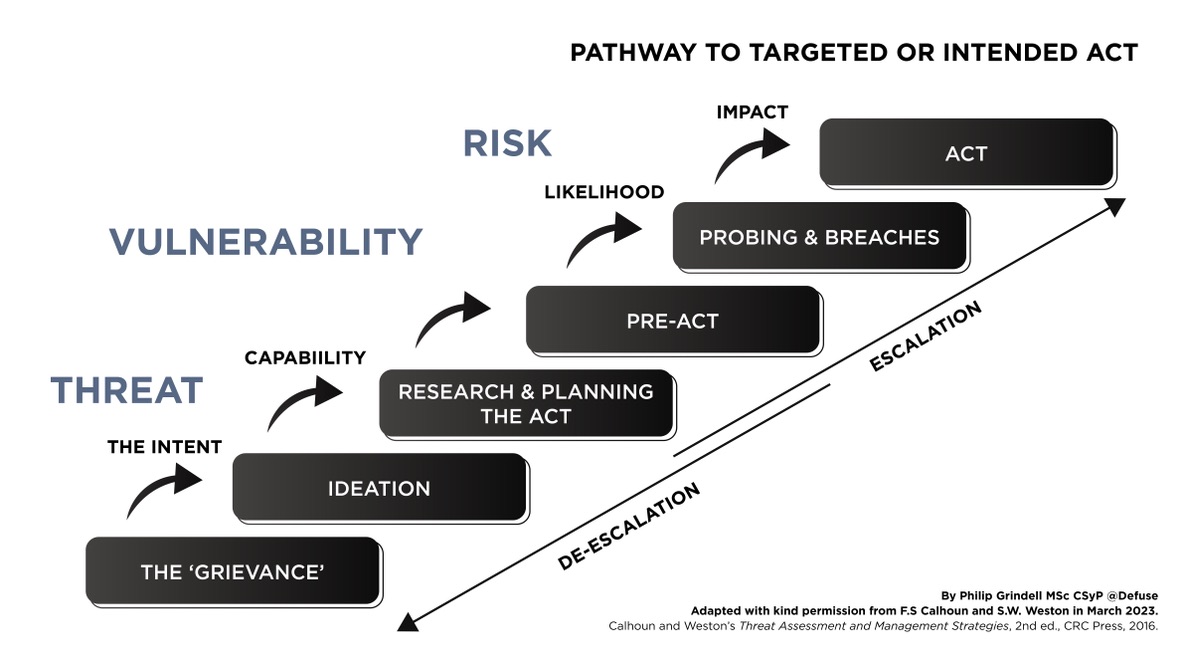
Once they have decided to act, they then follow a process known as the Pathway to Targeted or Indented Acts. It is during the process that they will conduct their research and planning seeking vulnerabilities and flaws in your security plan. They will identify where they can predictably find you at the desired time and the tactics they are going to use.
It is because they follow a process, that clues can be found and to the trained eye indicators identified.
The solution:
The first phase is to establish exactly what private information is publicly available and how that might be used as a vulnerability.
The type of information includes:
- Home addresses.
- Plans of the address.
- Details of any security measures.
- Schools children attend.
- Places of worship attended.
- Other venues regularly attended.
- Assets of value in the property.
- Breach data that can be used to conduct ID fraud etc.
Options:
To counter that we conduct a Digital Vulnerability Assessment (DVA).
The report aims to provide an initial threat assessment and recommended mitigation areas with elements of physical, online/digital security and a reputational risk focus.
Research is conducted replicating a range of potential threat actors (general public, criminals, journalists/media, through state actors).
Areas reviewed include key information, watchlist searches, contact details, dark web searches, associated businesses and organisations, social media, media / adverse media, and deep web/database presence.
Once an assessment is conducted, we can then identify mitigation opportunities.
DVAs are conducted by former members of the UK Intelligence, military, and Counter Terrorism experts, with decades of experience in bringing meaning to the data from Open Source as well as the Deep and Dark Web.
We also provide passive and proactive monitoring allowing us to track mentions/activity. We combine multi-source automated alerts and bespoke scrapers with analyst active engagement, enabling access to closed sources of relevance as needed.



